Amazon has added another set of new threat detections to its GuardDuty service in AWS. The three new threat detections are two new penetration testing detections and one policy violation detection.
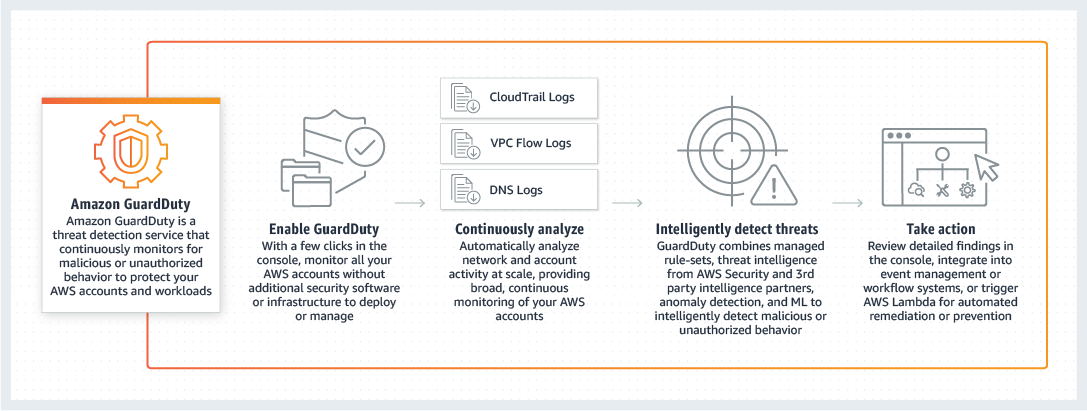
Amazon GuardDuty is a threat detection service available on AWS that continuously monitors for malicious or unauthorized behaviour to help customers protect their AWS accounts and workloads. When a threat is detected, the service will send a detailed security alert to the GuardDuty console and AWS CloudWatch Events – thus making alerts actionable and easy to integrate into existing event management and workflow systems.
Source: https://aws.amazon.com/guardduty/
According to a recent Techgenix article by Angela Karl on GuardDuty, the most important features of this service include:
- Account-level threat detection - accurately detect an account compromise with continuous monitoring in near real-time.
- Continuous monitoring across AWS accounts — monitor and analyze all AWS account and workload event data found on AWS CloudTrail, VPC Flow Logs, and DNS Logs without additional security software or infrastructure.
- Threat detections developed and optimized for the cloud - built-in detection techniques are specifically developed and optimized for the cloud. GuardDuty also has integrated threat intelligence with industry-leading third-party security partners, such as Proofpoint and CrowdStrike.
- Threat severity levels for efficient prioritization — features low, medium, and high threat severity levels so customers can respond accordingly.
With the three new threat detections, Amazon continues to grow the library of fully managed threat detections available for customers who enable Amazon GuardDuty in their AWS accounts. Moreover, Mid-November last year, Amazon also added three new threat detections:
- Two detections to help detect suspicious Tor Network-related activity
- A third to help customers identify cryptocurrency mining-related activity
Two of the recent three new threat detections are penetration testing related and will alert users to any machine running Parrot Linux or Pentoo Linux making an API call using your AWS credentials. These new extensions expand upon the existing Kali Linux detections.
The third new detection is a new policy violation detection, which alerts users to any request in which AWS account root credentials are used. Furthermore, this detection will inform users that root AWS account credentials are being used to make programmatic requests to AWS services, or login to the AWS Management Console.
More details on the availability of Amazon GuardDuty can be found on the AWS Regions page. Furthermore, the pricing details of this service are available on the pricing page.