The Cloud Native Computing Foundation (CNCF) Technical Oversight Committee (TOC) voted to accept CRI-O as an incubation-level hosted project on April 8th. CRI-O, created by Red Hat, is an Open Container Initiative (OCI) container runtime for Kubernetes that provides an alternative to Docker, rkt, or Moby.
CRI-O is designed to work specifically with Kubernetes by delivering a minimal runtime that implements the standard components of the Kubernetes Container Runtime Interface (CRI). Early versions of Kubernetes only supported containers with the Docker runtime. As the Kubernetes team began to add support for new runtimes, such as rkt, they decided to develop and release CRI in order to decouple Kubernetes from specific container runtimes.
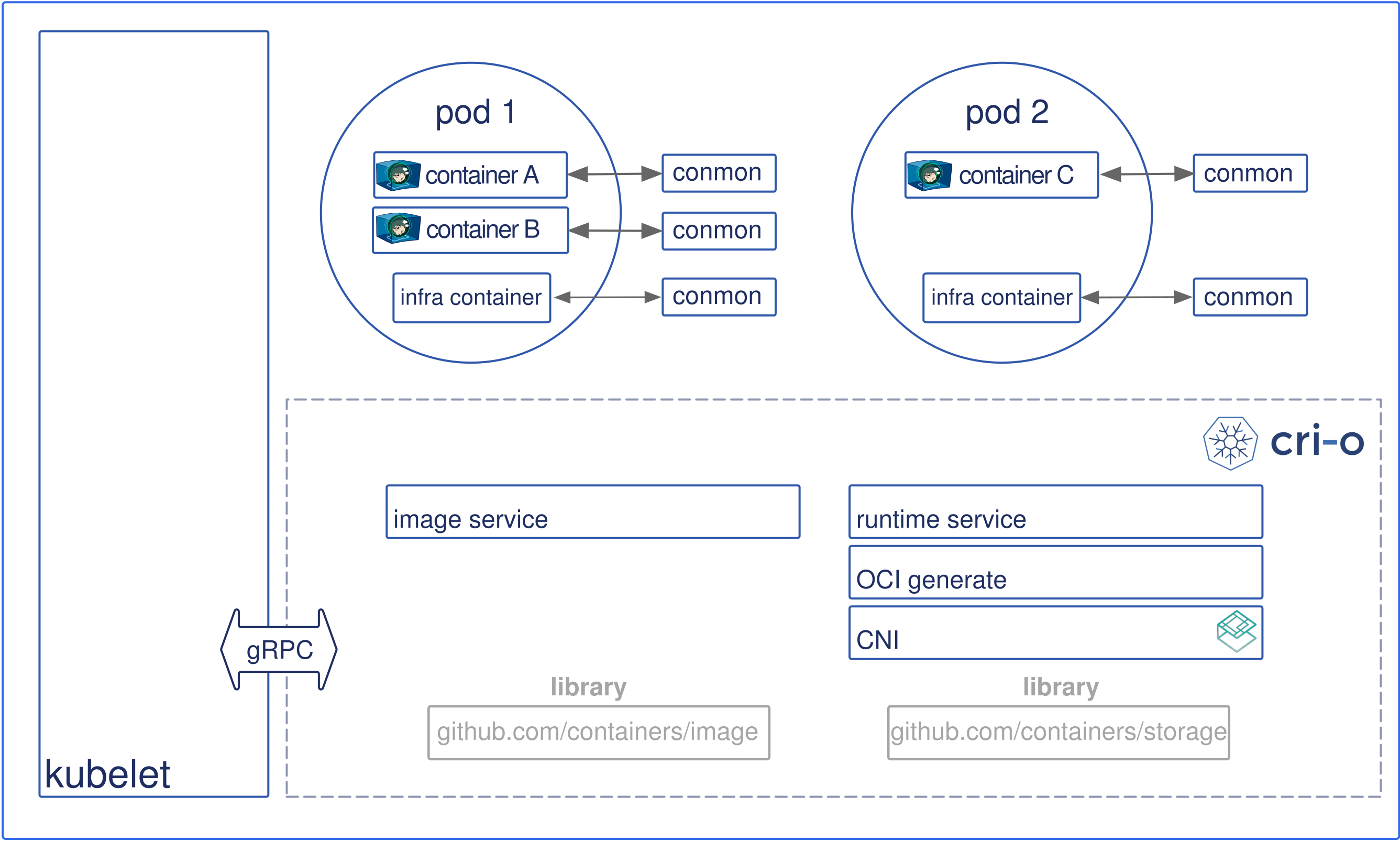
CRI is a plugin interface consisting of protocol buffers and a gRPC API that enables Kubernetes, via the kubelet, to communicate with any container runtime that satisfies the CRI interface. The two primary CRI RPCs are Image Service and Runtime Service, which specify how to pull an image and manage container lifecycles.
CRI-O enables Kubernetes to use any OCI-compliant runtime as the container runtime for running pods. Focused only on running containers in Kubernetes, the project scope is limited to the following:
- Support multiple image formats including the existing Docker image format
- Support for multiple means to download images including trust & image verification
- Container image management (managing image layers, overlay filesystems, etc)
- Container process lifecycle management
- Monitoring and logging required to satisfy the CRI
- Resource isolation as required by the CRI
The CRI-O runtime takes advantage of the Open Container Initiative, which provides a specification for the configuation, execution environment, and lifecycle of a container as well as a specification for the configuration, file system, index, and manifest of an image. To manage container images and storage, CRI-O uses the containers/image and containers/storage libraries from the open source Containers project, which includes several container tools. The two containers libraries are used for pulling images from an image registry and storing the image contents in the container filesystem.
CRI-O networking is implemented with the Container Networking Interface, another CNCF project that provides specifications and libraries for configuring network interfaces in Linux containers. Containers are monitored with the internal tool cronmon, which collects container logs and records exit codes.
According to the CRI-O project, a primary benefit of CRI-O is stability in the Kubernetes ecosystem, with a commitment to passing Kubernetes tests. CRI-O is developed with branches for each Kubernetes release and developed alongside the Kubernetes release and deprecation cycles. The CRI-O codebase contains end to end testing against Kubernetes that runs on every pull request and must pass before PRs are accepted.
CRI-O began development in 2016, after the Kubernetes project introduced CRI, and CRI-O 1.0 was released in 2017. Currently, CRI-O supports runc and Kata Containers as container runtimes with the possibility that any OCI-comnpliant runtime is potentially plugable. CRI-O supports OCI container images and can pull from any container registry. Core contributors include RedHat, Intel, SUSE, Hyper, and IBM.
Information on getting started with CRI-O and how to contribute can be found at the CRI-O Github project.