In a recent blog post, Microsoft announced the general availability of Sentinel, a Security Information and Event Management (SIEM) service in Azure, providing customers with intelligent security analytics across their enterprise. With the GA of Azure Sentinel, Microsoft now enters the SIEM market.
Earlier this year in March, InfoQ reported on the first announcement of Azure Sentinel, the main feature being the use of machine learning and artificial intelligence (AI) to analyze incoming data and adapt to evolving threats. Since then, more than 12,000 customers have joined the Preview program, and Microsoft has continued investing in the service as the GA release now comes with several new features.
Like many SIEM services, Azure Sentinel pulls large volumes of data from users, applications, servers, and devices running on-prem or in the cloud. Microsoft integrated Sentinel with Microsoft services like Azure Security Center, Azure Active Directory, and Microsoft 365. Moreover, now with the GA release, Microsoft created new connectors for their services such as Cloud App Security and Information Protection next to a growing list of third-party connectors including Cisco, Check Point, Palo Alto Networks, and Symantec.
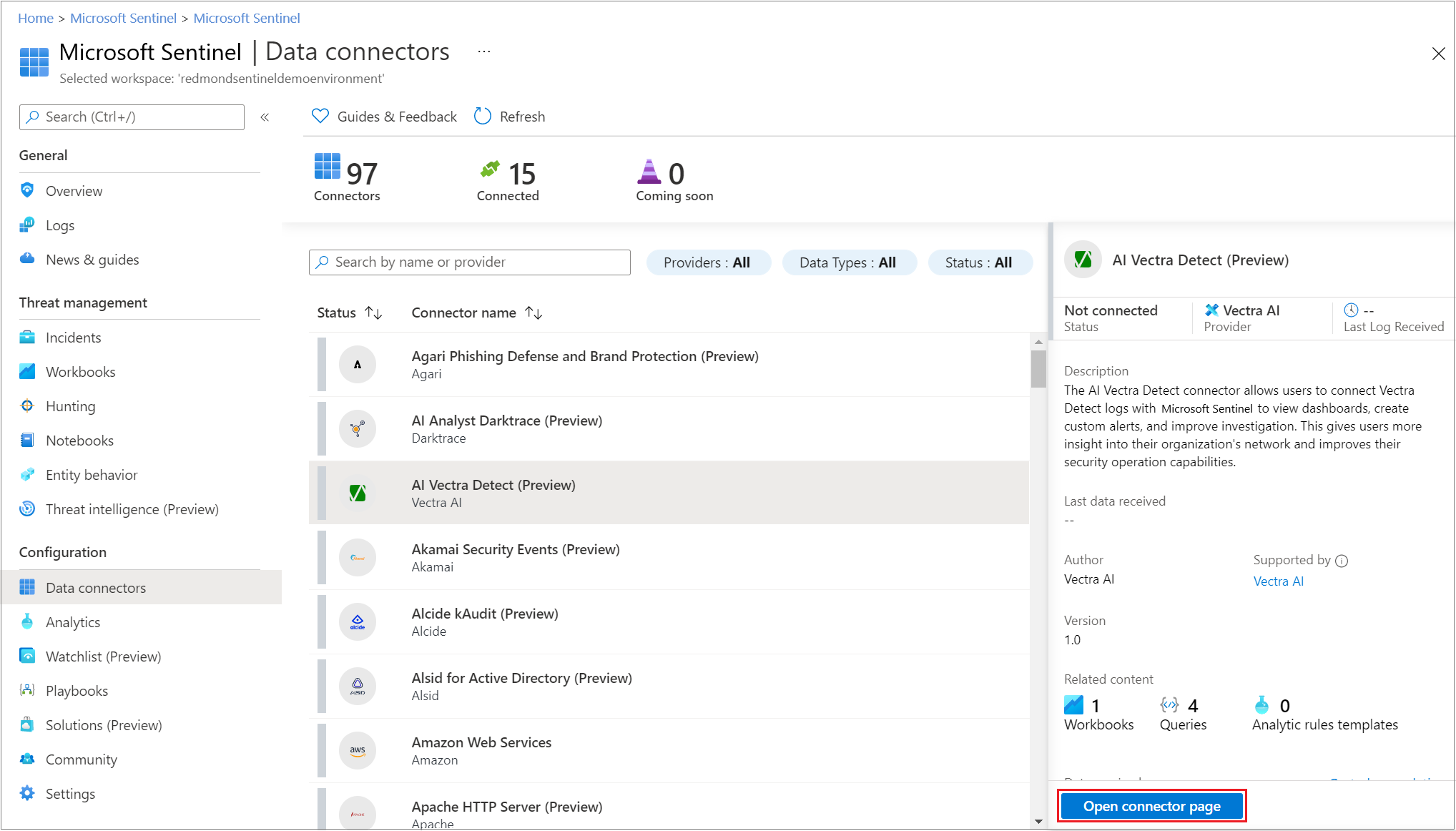
Source: https://docs.microsoft.com/en-us/azure/sentinel/overview
Next, to the connectors allowing customers to ingest data from across the enterprise, Microsoft also added the following:
- More than 100 built-in alert rules, and the use of the new alert wizard to create custom rules.
- A preview of a new machine learning model that identifies suspicious logins across Microsoft identity services to discover malicious SSH accesses.
- Another preview of a new machine learning model called Fusion to connect data from multiple sources, like Azure AD anomalous logins and suspicious Office 365 activities, and to detect 35 different threats that span different points on the kill chain.
- A rich "hunting interface" for users that features a growing collection of hunting queries, exploratory queries, and Python libraries for use in Jupyter Notebooks.
- A new rules wizard allowing users to decide which Microsoft alerts trigger the creation of an incident.
- A new investigation graph preview, which allows users to visualize and traverse the connections between entities like users, assets, applications, or URLs and related activities like logins, data transfers, or application usage, in order to rapidly understand the scope and impact of an incident.
- New actions and playbooks simplify the process of incident automation and remediation using Azure Logic Apps.
Pricing starts with a pay-as-you-go option of $2.46 per gigabyte (GB) of data analyzed by Azure Sentinel. More details on the pricing of Azure Sentinel are available on the pricing page.