At re:Invent 2022, AWS released a new enterprise application connectivity service, Verified Access. The service provides Zero Trust access to enterprise web applications by employing endpoints and policies to authenticate and authorize user requests against identity providers or device management systems. Verified Access is currently in public preview in 10 AWS regions.
Zero Trust is a security model that requires all access to resources to be continuously evaluated regardless of the source of the access request. The model was popularized by Google in the aftermath of a cyberattack in 2009 named Operation Aurora. Zero Trust is often compared with traditional network security, based on a castle-and-moat concept, in which most protections would be deployed to prevent unauthorized access to the network and trust would be assumed within the network.
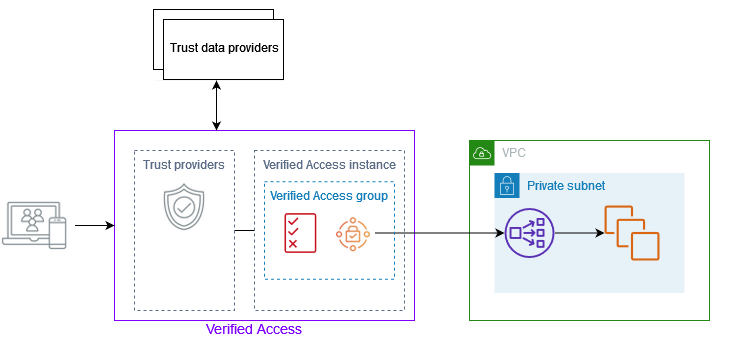
In traditional network security models, a Virtual Private Network (VPN) connection is the primary mechanism granting access to enterprise web applications by allowing remote users to "appear" within the network. With Verified Access, the need for a VPN is eliminated as the user’s request is evaluated when accessing applications via a Verified Access endpoint’s domain on their web browser. When the user request is received by a Verified Access instance, it directs users to authenticate with its registered Trust Providers and then evaluates the Trust data against stored policies for the Verified Access group. Verified Access supports user-identity trust providers, such as OIDC providers or AWS IAM Identity Center, and device-based trust providers, which include device management systems like Jamf and Crowdstrike. If the evaluation is successful the user request is then directed towards the application target which could be a Load Balancer or an Elastic Network Interface.
While elements of Zero Trust for enterprise web applications could be implemented with existing AWS Services, for example Application Load Balancer authentication with AWS Cognito or OIDC Providers, users have welcomed an integrated solution as @scalefactory writes in a tweet:
AWS Verified Access, now in Preview, is a zero trust proxy allowing access to internal applications without needing a VPN. We've been doing something like this using Lambda features provided by CloudFront and ALB, but a formal solution looks good.
Despite the warm reception, a criticism of the service thus far has been its costs. With a per-application and per-hour pricing model of $0.27, an estate with 20 corporate applications could cost just under $48,000. Jason Garbis, chief product officer at Appgate, comments in a review:
If you have 100 applications it’s … a considerable investment and if you have hundreds of applications this could get very expensive very quickly . . and also think about whether this solution makes sense compared to perhaps other Zero Trust solutions that can tie-in to your identity provider.
Other solutions commonly considered as alternatives to AWS Verified Access would be Google’s Identity Aware Proxy, Cloudflare’s Access or Teleport’s Application Access.
AWS Verified Access is currently available in preview in 10 AWS Regions: US East (Ohio, N. Virginia), US West (N. California, Oregon), Asia Pacific (Sydney), Canada, Europe (Frankfurt, Ireland, London), and South America (São Paulo).