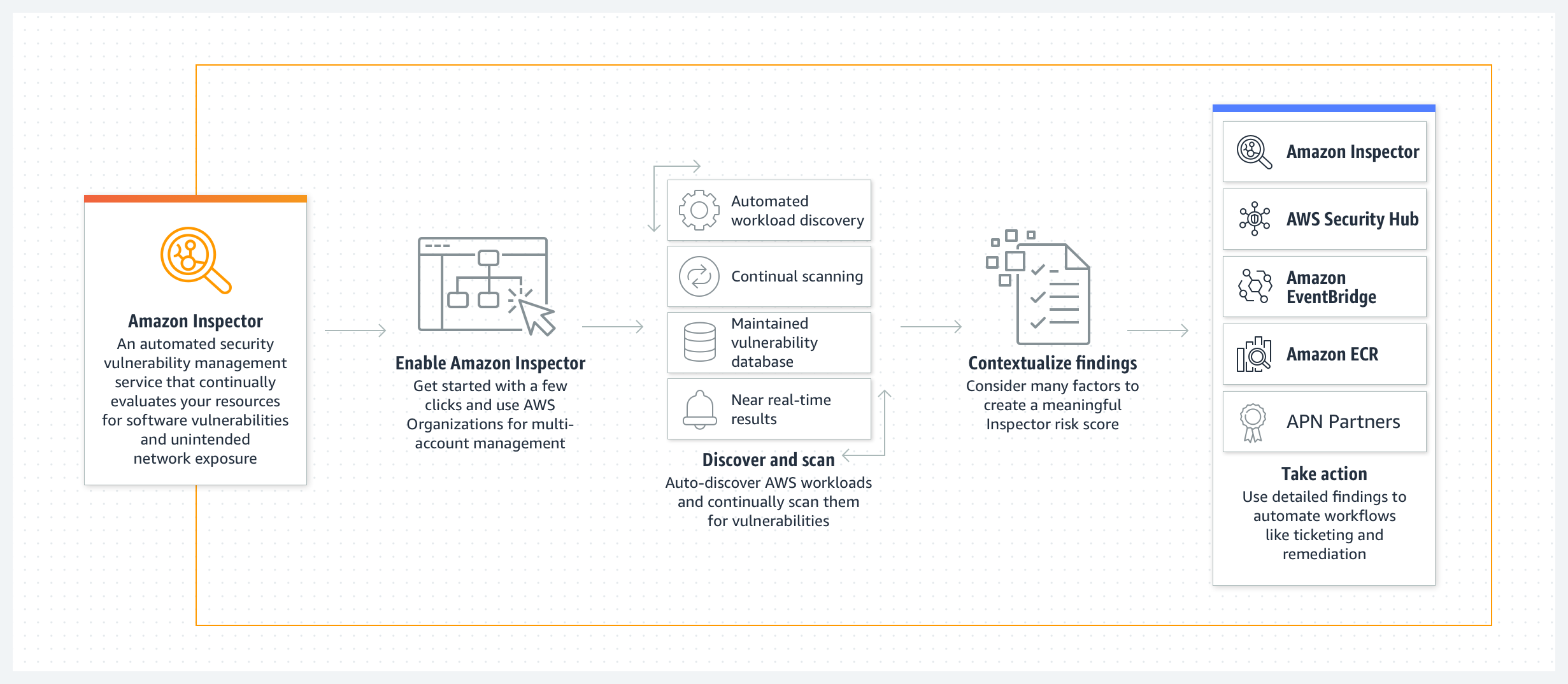
Amazon Inspector is an automated vulnerability management service that continually scans AWS workloads for software vulnerabilities and unintended network exposure. It was first launched in 2015, and during the recent re:Invent 2021, AWS re-launched it with brand new architecture and a host of new features such as container-based workloads, integration with Amazon Event Bridge, and AWS Security Hub.
The new Amazon Inspector is the outcome of the service's development team addressing new objectives such as large-scale deployment, support for a broader range of resource types that need to be assessed, and a need to discover and rectify issues quickly. With the new Amazon Inspector, customers now only need to enable the service – and it will auto-discover and start continual assessment of their EC2 and Amazon Elastic Container Registry-based container workloads to evaluate their security posture, even as the underlying resources change.
Steve Roberts, a developer advocate, focused on .NET and PowerShell development on AWS, explains in an AWS news blog post:
EC2 instances are discovered and assessed for unintended exposure to external networks and software vulnerabilities using the Systems Manager agent, already included by default in images provided by AWS for instance management, automated patching, and more. Container-based workloads are assessed as the images are pushed to Amazon Elastic Container Registry. Without needing additional software or agents, container images and EC2 instances are assessed in near real-time when an event occurs.
Source: https://aws.amazon.com/inspector/
The new Amazon Inspector collects events from over 50 vulnerability intelligence sources, including CVE, the National Vulnerability Database (NVD), and MITRE. Furthermore, Amazon Inspector has partnered with Snyk to receive additional vulnerability intelligence for its vulnerability database – and Amazon Inspector Partners like Palo Alto have integrated their products to help further customers operationalize Inspector findings. Additionally, AWS Level 1 MSSP Partners such as Cloudhesive and Deloitte offer their customers services to manage Inspector findings.
The automated assessment is driven by changes in workload configuration and newly published vulnerabilities – only addressed when needed. Any image that may be affected by a recently identified entry, for example, a new CVE notification, will be automatically rescanned - and image rescanning is enabled for 30 days from the date they are pushed to the registry. And finally, customers can also enable an option to only scan on image push and not subsequently perform rescans.
With the recent zero-day exploit discovered in log4j, Nick Coult, general manager for Amazon ECR and Amazon ECR Public at AWS, tweeted:
If you are looking to mitigate the log4j vulnerability in your container images, Amazon ECR with Amazon Inspector scanning is capable of detecting the presence of vulnerable versions of log4j in your images. It shouldn't be the only thing you do to detect, but it might help!
The new Amazon Inspector is currently available in 19 AWS Regions, and pricing is based on the number of container image scans run and the average number of EC2 instances scanned. More details on pricing are available on the pricing page.