Azure Cosmos DB is a globally-distributed and fully-managed NoSQL database service. Recently, Microsoft warned thousands of its Cosmos DB customers of a vulnerability that exposes their data. A flaw in the service could grant a malicious actor access keys to steal, edit or delete sensitive data.
A team of researchers of the Tel Aviv-based Wiz.io discovered the security flaw, dubbed it ChaosDB, and disclosed it to Microsoft earlier this month. They could exploit Cosmos DB through the Jupyter Notebook feature added to Cosmos DB back in 2019. This feature allows Cosmos DB customers to visualize their data and create customized views.
Microsoft turned the Juypter Notebook feature on by default for all Cosmos DB instances in February of this year. However, according to a recent Wiz.io blog post, their researcher could find misconfigurations in the feature and exploit them:
In short, the notebook container allowed for a privilege escalation into other customer notebooks. As a result, an attacker could gain access to customers' Cosmos DB primary keys and other highly sensitive secrets such as the notebook blob storage access token.
An attacker can leverage the access keys for full admin access to all the data stored in the affected Cosmos DB accounts. Moreover, the attacker can control the customer Cosmos DB directly from the internet, with full read/write/delete permissions.
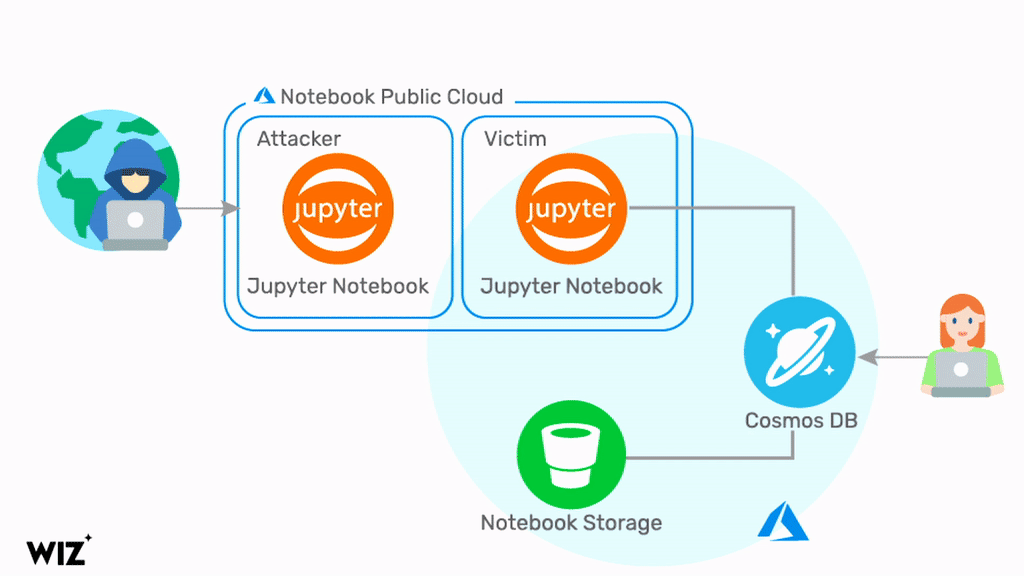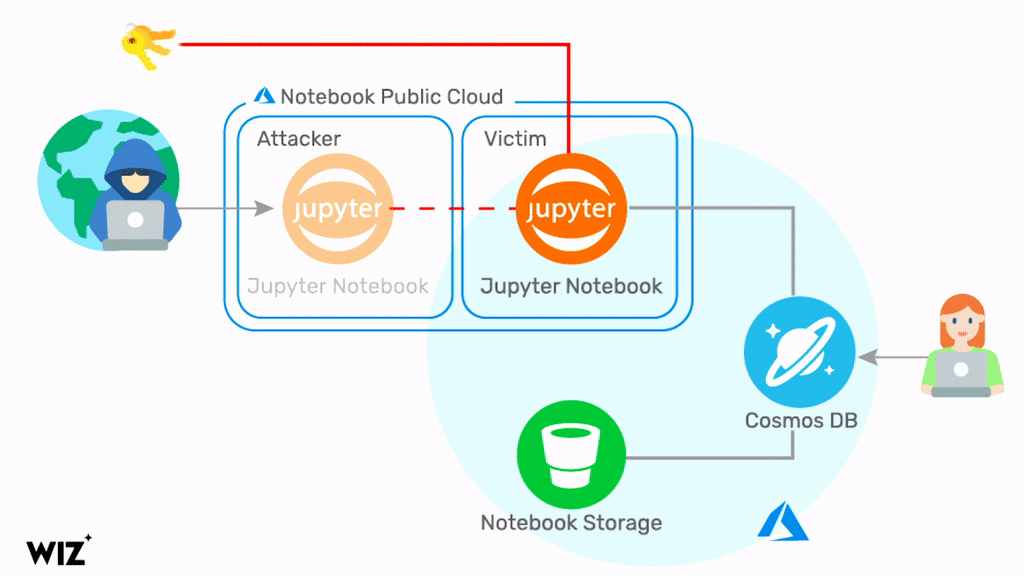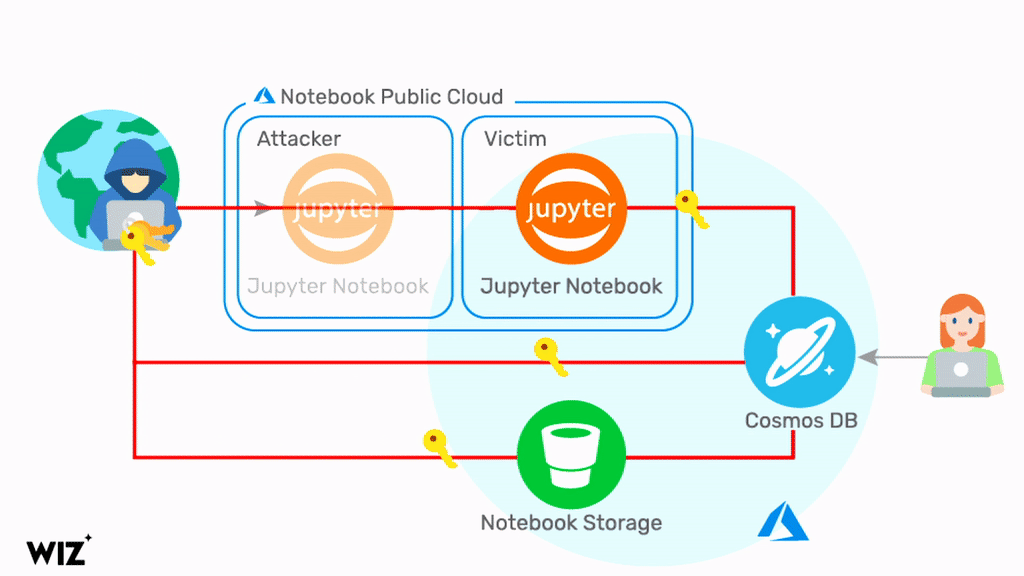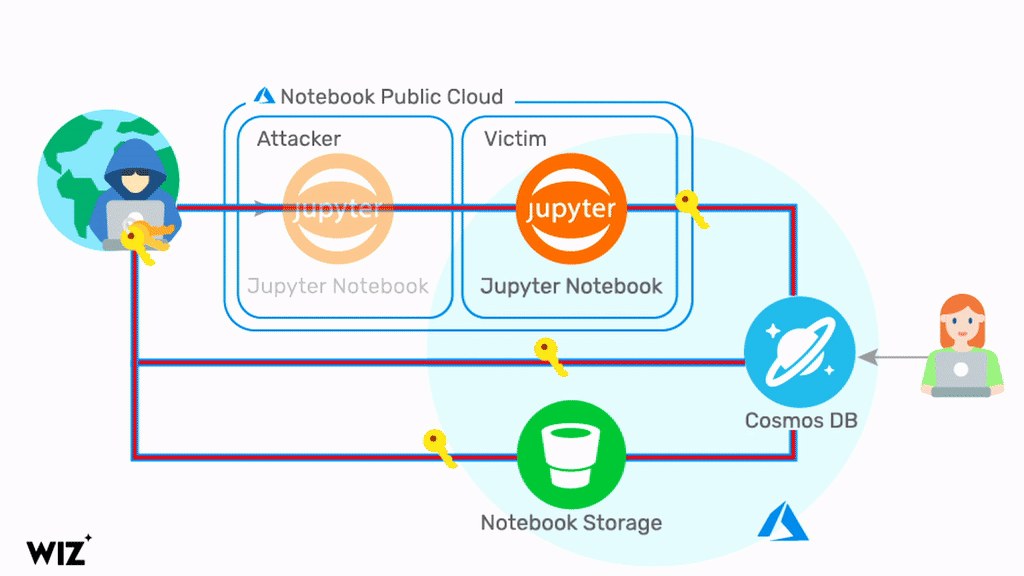
Source: https://chaosdb.wiz.io/
Wiz.io notified Microsoft's Security Team about the exploit, who took immediate action turning the feature off. Furthermore, the company emailed all affected customers advising them to change the access. In a recent Microsoft Security Center blog post on the vulnerability, the security team states:
Our investigation indicates that no customer data was accessed because of this vulnerability by third parties or security researchers. We've notified the customers whose keys may have been affected during the researcher activity to regenerate their keys.
Since the vulnerability has been exploitable for months, more Cosmos DB customers are at risk than the ones Microsoft notified, according to the Wiz blog post. Furthermore, several media channels picked up the vulnerability story, and discussions on social media are vibrant.
A respondent on a Hacker News thread stated some concerns regarding the exploit:
Putting aside this specific failure, the way all the cloud providers are trying to interconnect their service offerings makes me increasingly nervous. It is too easy to accidentally grant overly permissive IAM policies without realizing it.
In addition, hacker Dino A. Dai Zovi stated in a tweet:
This type of cross-tenant attack against Azure's Cosmos DB is a great example of why you should want client-side, app-layer encryption in your services so that your datastores primarily store ciphertext of any sensitive data.
Lastly, in January 2021, the US Cybersecurity and Infrastructure Security Agency (CISA) published a report to alert companies using cloud services:
Threat actors are using phishing and other vectors to exploit poor cyber hygiene practices within a victims' cloud services configuration.
The Cosmos DB vulnerability is another example of how accurate the threat of exploits still is.